Lead gen fraud
Device spoofing
Bad actors will produce worthless engagement (clicks, form fills with stolen information, etc.) on a single device. However, a large volume of activity from the same device and cookie is easily detectable as fraud. In order to fool advertisers, bad actors will spoof their browser and operating system (OS) and reset cookies, effectively allowing one device to impersonate many.
How they do it
- Malicious publisher has registered for advertiser’s lead gen campaign
- Malicious publisher’s site features a fake form fill, capturing the relevant personally identifiable information (PII) to satisfy advertiser’s lead gen criteria
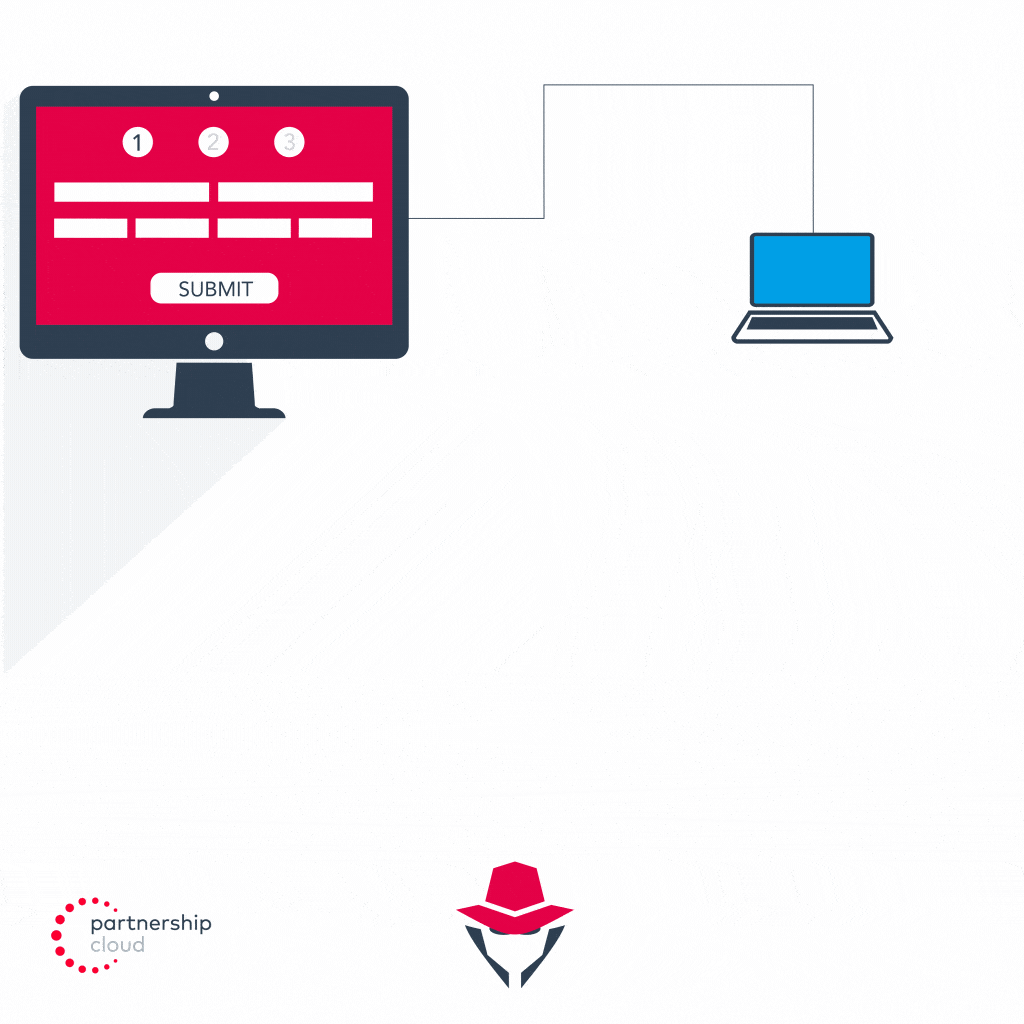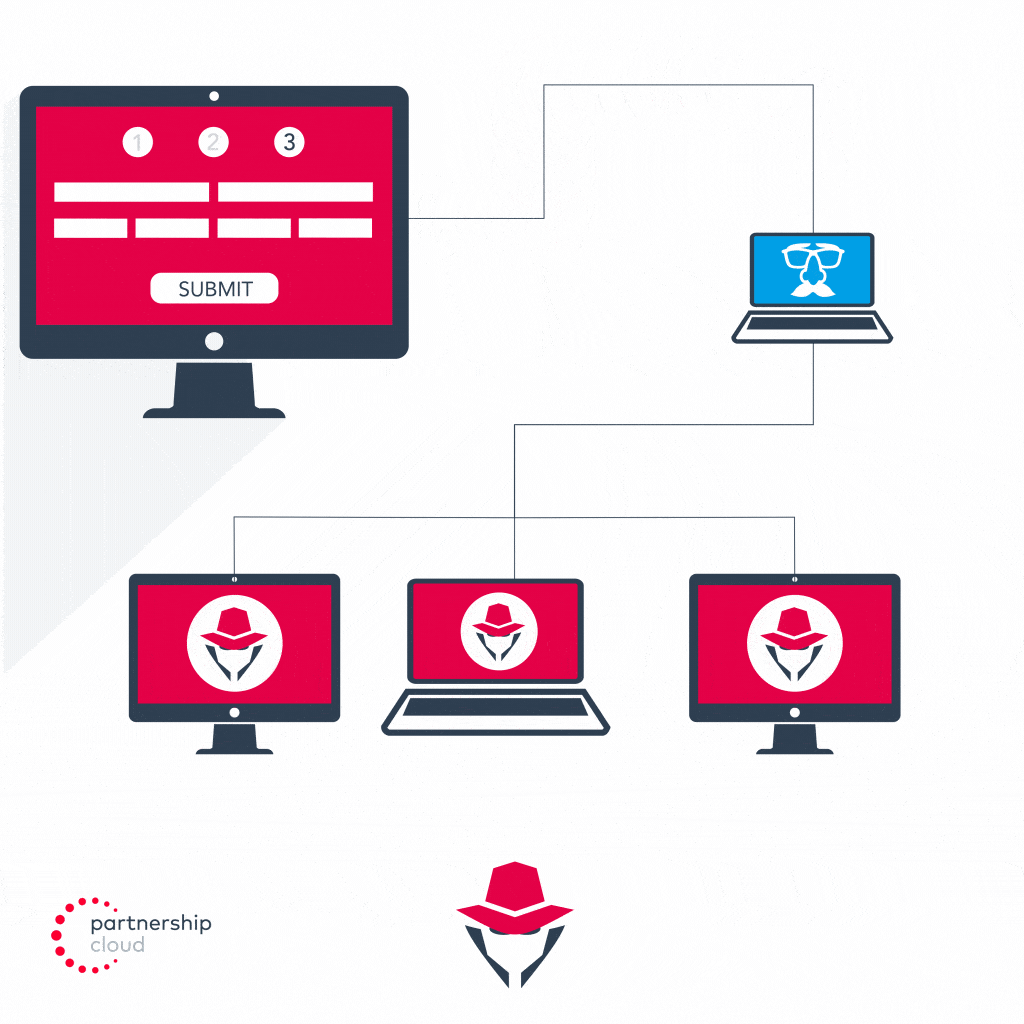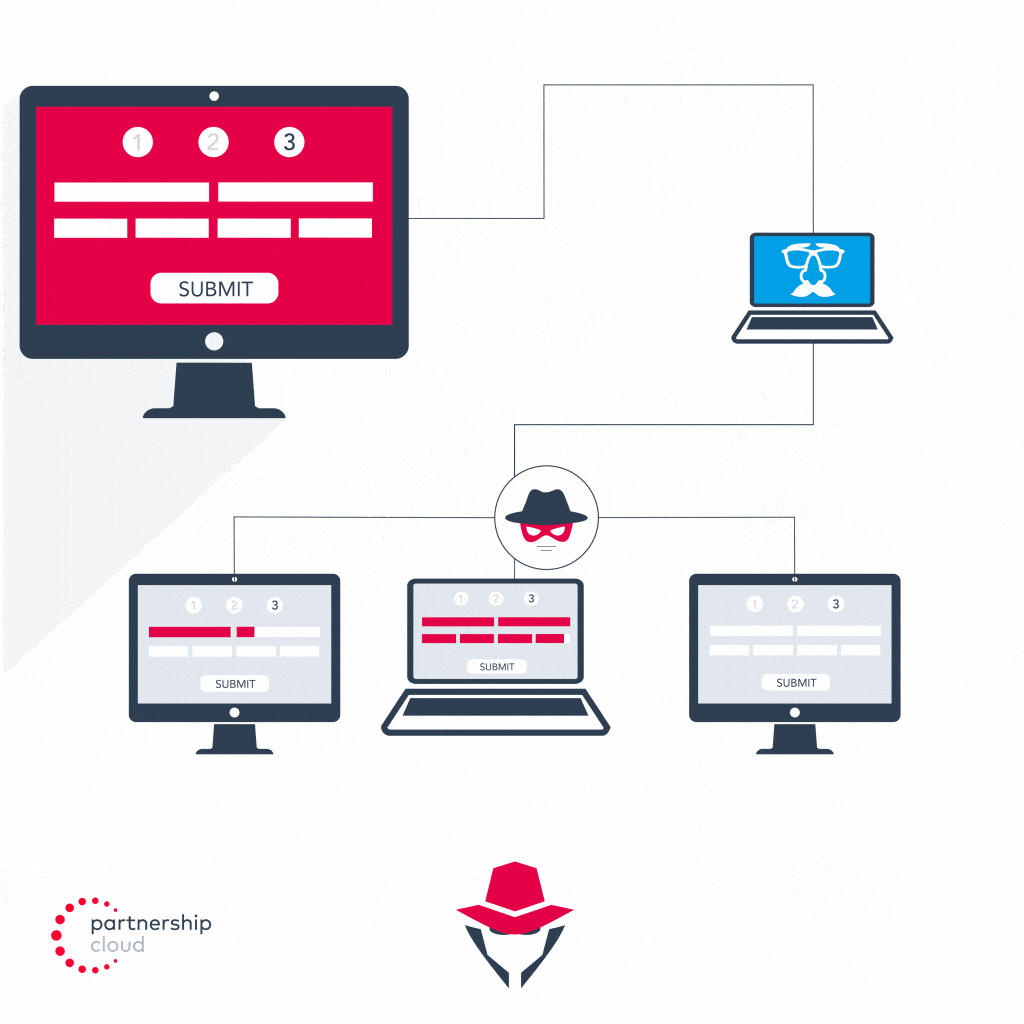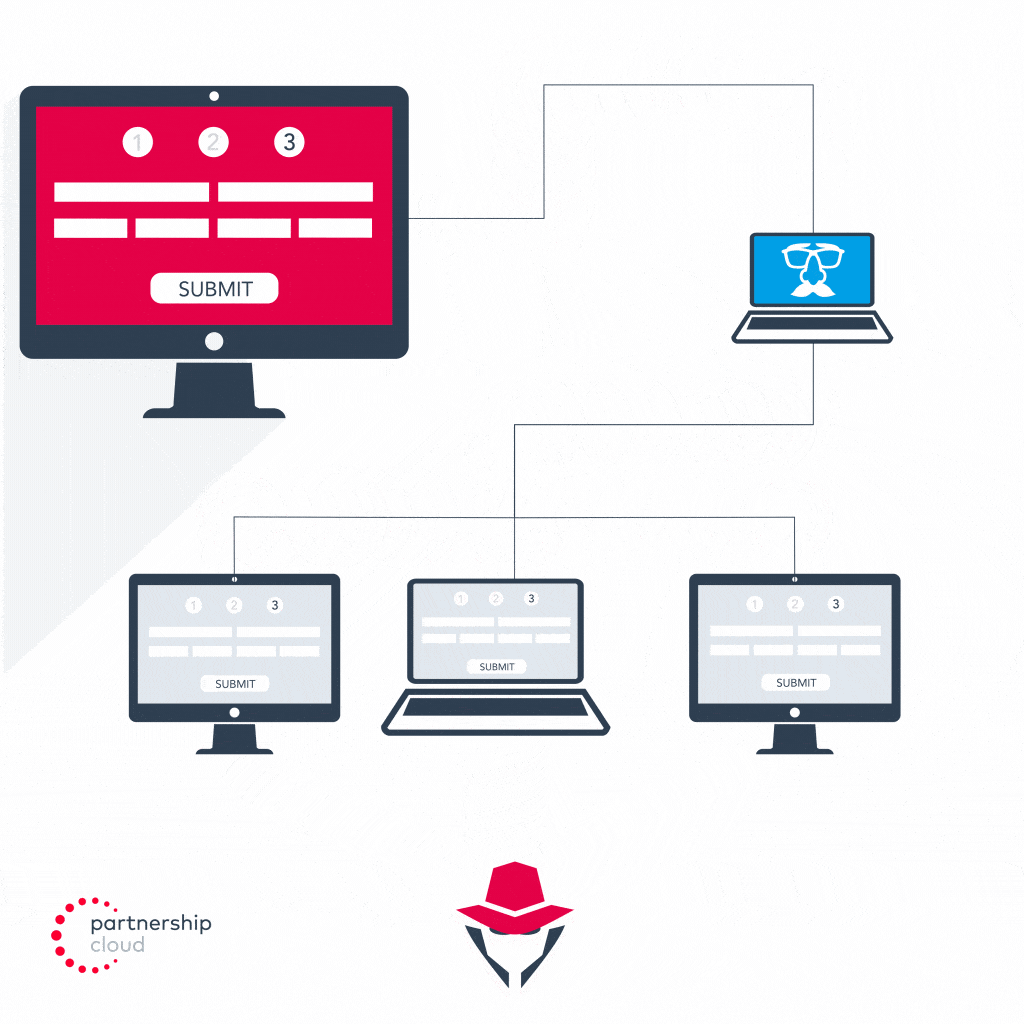
- Malicious publisher uses emulator to send large volumes of automated traffic, first to publisher’s site and then to advertiser’s site
- Malicious Publisher auto populates the real user information stolen through its fake form fill into the advertiser’s actual form fill and submits the lead
- Malicious publisher simultaneously misrepresents emulator’s device ID to make the leads appear as if they are coming from multiple legitimate devices
- Advertiser attributes credit to malicious publisher for each lead generated, even though they provided automated traffic and submitted stolen information, and pays malicious publisher per lead submitted